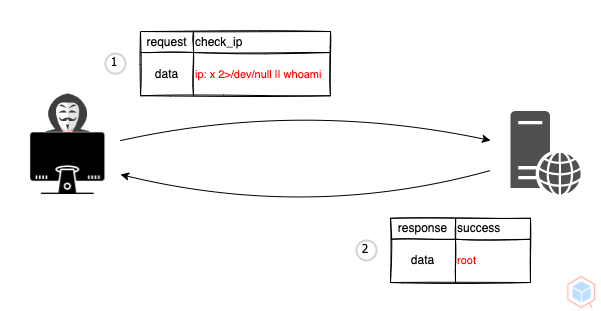
A threat actor may inject arbitrary operating system (OS) commands on target
- Threat actor crafts a malicious request to a vulnerable target
- The target process the malicious request and returns the result
$result = exec("ping -c4 ".$_GET["ip"]);
echo($result)x 2>/dev/null || whoami
root
High
- Command Injection
- Read & write data
- Command execution
- Input validation
154d5db5-9614-42f9-9898-3355a7b7848f