The default password for the application is R00t. Please ensure to change it immediately after installation to enhance security.
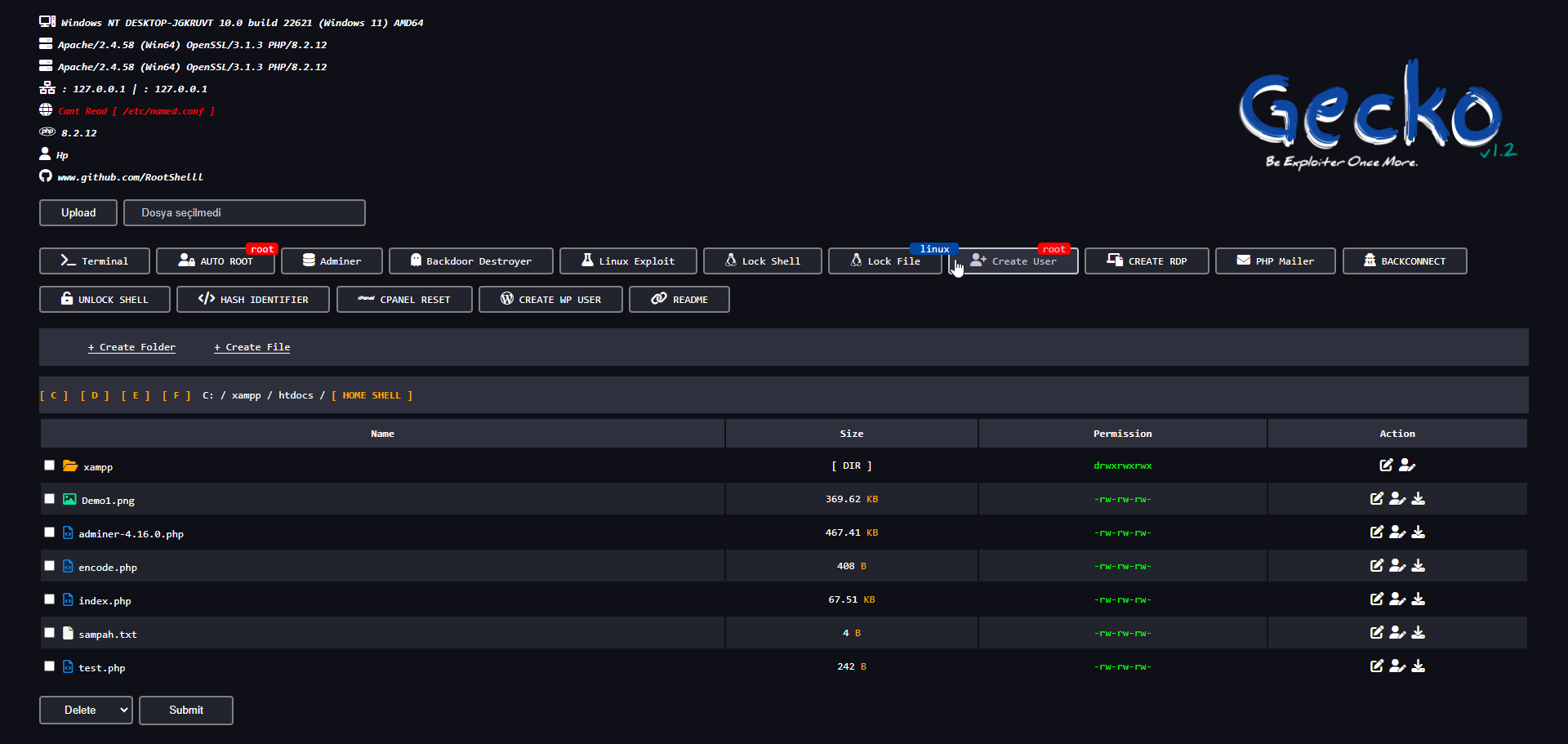
R00tGecko is an advanced web backdoor tool designed to bypass security measures, provide root access, and manage shells. It offers a wide range of features for users who need to exploit security weaknesses and gain full control over compromised servers.
- Bypass Errors: Seamlessly bypass 403, 404, and 500 errors.
- Linux Exploit Suggester: Suggests potential exploits for Linux systems.
- Backdoor Destroyer: Removes any existing backdoors to secure the system.
- Auto Root with Pwnkit: Automatically gain root access to Linux servers.
- Add Admin User to WordPress: Add a new admin user to a compromised WordPress site.
- Lock Shell & File: Secure shells and files to prevent unauthorized access.
- Cpanel Reset and Backconnect: Includes Cpanel reset, Adminer, and backconnect features.
- Hash Identifier: Identifies different hash types.
- Archive Compressor/Decompressor: Compress and decompress archives effortlessly.
- No Detection Shell: Ensures your shell remains undetected.
To install and configure Gecko, follow these steps:
-
Download Gecko: Download the Gecko tool from GitHub.
-
Upload Gecko-Shell.php: Upload the
Gecko-Shell.phpfile to your target server. -
Access the File: Open the uploaded file in your browser and use the various tools provided by Gecko.
Always use this tool responsibly. We are not responsible for any illegal activities.
Gecko can bypass common errors like 403, 404, and 500 to ensure unimpeded access, even if strict security settings are in place.
Gecko automates root access to Linux servers using tools like Pwnkit, allowing privilege escalation and full system control.
For WordPress targets, Gecko enables the addition of a new admin user to the WordPress installation. This helps in gaining admin privileges on compromised sites.
Gecko’s backdoor destroyer feature ensures that no malicious files remain by removing previously created backdoors after use.
Gecko can be used for:
- Penetration Testing: Perform authorized penetration testing and vulnerability assessments on your own systems.
- Remote Shell Management: Manage and maintain access to remote shells in testing scenarios.
- Security Research: Conduct security research and simulate exploitation on your own infrastructure.
Important: Always adhere to ethical hacking practices. Ensure you have permission before testing or deploying any of these tools on external servers or websites.
Feel free to fork this repository and contribute to the ongoing development of Gecko. We welcome contributions that improve security, expand features, or enhance documentation.
Gecko is licensed under the MIT License.